Suppress detections with tuning parameters
Provide information about your network environment so that the ExtraHop system can suppress low-value or redundant detections from ever being generated.
You can add criteria from the Tuning Parameters page or directly from a detection card. In addition, you can specify network localities, which classify IP address ranges as internal or external to your network.
| Video: | See the related training: Configure Tuning Parameters |
Specify tuning parameters for detections and metrics
Specify tuning parameters to improve metrics and suppress low-value detections from ever being generated.
| Note: | The fields on this page might be added, deleted, or modified over time by ExtraHop. |
- Log in to the ExtraHop system through https://<extrahop-hostname-or-IP-address>.
-
Click the System Settings icon
 and then click Tuning
Parameters.
and then click Tuning
Parameters.
-
Specify values for any of the following parameters available on the page.
Option Description Gateway Devices By default, gateway devices are ignored by rules-based detections because they can result in redundant or frequent detections.
Select this option to identify potential issues with gateway devices such as your firewalls, routers, and NAT gateways.
This setting does not affect machine-learning detections.
Outbound Tor Nodes By default, outbound connections to known Tor nodes are ignored by rules-based detections because they can result in low-value detections in environments with minimal Tor traffic.
Select this option to identify detections on outbound connections to known Tor nodes if your environment observes substantial outgoing Tor traffic.
Inbound Tor Nodes By default, inbound connections from known Tor nodes are ignored by rules-based detections because they can result in low-value detections in environments with minimal Tor traffic.
Select this option to identify detections on inbound connections from known Tor nodes if your environment observes substantial incoming Tor traffic.
Accelerated Beaconing Detection By default, the ExtraHop system detects potential beaconing events over HTTP and SSL.
Select this option to detect beaconing events faster than the default detection.
Note that enabling this option can increase the detection of beaconing events that are not malicious.
IDS Detections By default, ExtraHop systems with connected Intrusion Detection System (IDS) sensors only generate detections for traffic inside your network. Select this option to generate IDS detections for traffic that is inbound from an external endpoint.
Note that enabling this option can significantly increase the number of IDS detections.
Privileged Active Directory Accounts Specify regular expressions (regex) that match privileged Active Directory accounts in your environment. The parameter list includes a default list of regular expressions for common privileged accounts that you can edit.
The ExtraHop system identifies privileged accounts and tracks account activity in Kerberos records and metrics.
Allowed Public DNS Servers Specify public DNS servers allowed in your environment that you want rules-based detections to ignore.
Specify a valid IP address or CIDR block.
Allowed HTTP CONNECT Targets Specify URIs that your environment can access through the HTTP CONNECT method.
URIs must be formatted as <hostname>:<port number>. Wildcards and Regex are not supported.
If you do not specify a value, detections that rely on this parameter are not generated.
Trusted Domains Add legitimate known domains to the Trusted Domains list to suppress future detections that target malicious domain activity for that domain.
Type a single domain name per field.
If you specify a domain name, the tuning parameter suppresses detections for all subdomains. For example, if you add example.com as a trusted domain, detections with vendor.example.com as the offender are also suppressed. If you add a subdomain such as vendor.example.com, the parameter only suppresses detections where the participant ends with that exact subdomain. In this example, test.vendor.example.com would be suppressed but test.example.com would not.
Wildcards and Regex are not supported.
To add more than one trusted domain name, click Add Domain.
For detections that have an associated domain, you can also add a trusted domain directly from a detection card.
- Click Save.
Add a tuning parameter from a detection card
If you encounter a low-value detection, you can add tuning parameters directly from a detection card to keep similar detections from generating.
Before you begin
Users must have full write or higher privileges to tune a detection.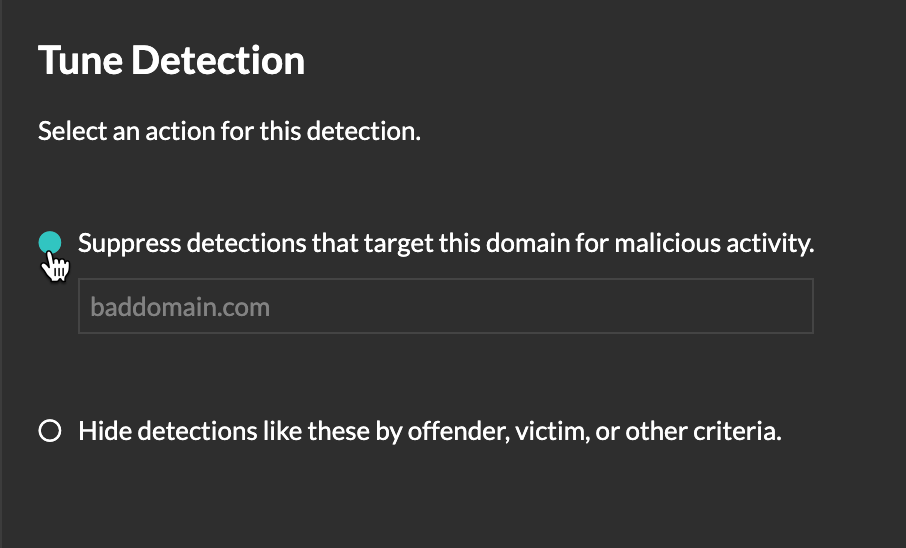
Thank you for your feedback. Can we contact you to ask follow up questions?