Add your own identity provider to Reveal(x) 360
The Reveal(x) 360 system includes a default identity provider that enables you to manage your users who access the ExtraHop system. If your company already has an identity provider (IdP) that supports SAML 2.0, you can configure the IdP to manage your users on the ExtraHop system.
Before you begin
You must have an ExtraHop user account with System and Access Administration privileges to configure Reveal(x) 360.- SAML 2.0
- Support SP-initiated login flows. IdP-initiated login flows are not supported.
- Support signed SAML Responses
- Support HTTP-Redirect binding
| Tip: | These procedures require you to copy and paste information between the ExtraHop system and your IdP, so it is helpful to have each system open side-by-side. |
Review Reveal(x) 360 access types and privilege levels
There are three types of access, each with their own privilege levels, that you can grant to your users in Reveal(x) 360: user privilege access, packets and session keys access, and detections access.
Familiarize yourself with the following access types and their associated privilege levels. You will map attribute names between both systems in the procedures in this guide.
See User privileges to learn what users can do in each privilege level in Reveal(x) 360.
- User privilege access
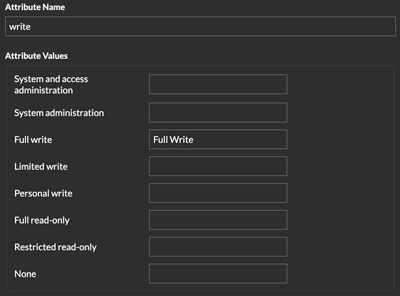
- Grants users read and write privileges throughout the system. There are 8 available privilege levels: system and access administration, system administration, full write, limited write, personal write, full read-only, restricted read-only, and none.
- Packets and session keys access
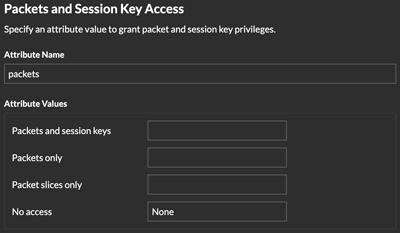
- Grants users the ability to view and download packet captures, with or without the ability to download session keys: No access, Packet slices only, Packets only, or Packets and session keys.
- Detections access
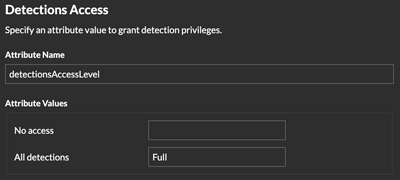
- Grants users the ability to view detections: No access or Full access.
If you only want to grant your users access to privilege levels for Full write and Full read-only, no packet access, and full detection access, create a worksheet similar to the following example:
| Access Type | Privilege Level Name in Reveal(x) 360 | Attribute Value in your IdP |
|---|---|---|
| User privilege access | Full write | Full Write |
| User privilege access | Full read-only | Read-Only |
| Packets access | No access | None |
| Detections access | Full access | Full |
Create an application in your IdP
- Log into Reveal(x) 360.
-
Click System Settings
 at the top right of the page and then click
All Administration.
at the top right of the page and then click
All Administration.
- Click User Access.
- Note the Assertion Consumer Service (ACS) URL and Entity ID, which you will paste into your IdP configuration.
- Paste the ACS URL from Reveal(x) 360 into the ACS URL field on your IdP.
- Paste the SP Entity ID from Reveal(x) 360 into the SP Entity ID field on your IdP.
Next steps
Leave the IdP settings open and configure attribute mappings next.Configure attributes that identify the user
You must configure attributes on your IdP that identify the user throughout the ExtraHop system by their first name, last name, and email address. Refer to your identity provider documentation for the correct property names when mapping these attributes or attribute statements.
- In the application attribute mapping section, add three attributes.
- In the first attribute, select email or similar. (For example, in Okta, this attribute is called user.email.)
- For the Service Provider, paste the following string: urn:oid:0.9.2342.19200300.100.1.3
- In the second attribute, select last name or similar. (For example, in Okta, this attribute is called user.lastName.)
- For the Service Provider, paste the following string: urn:oid:2.5.4.4
- In the third attribute, select first name or similar. (For example, in Okta, this attribute is called user.firstName.)
- For the Service Provider, paste the following string: urn:oid:2.5.4.42
| Service Provider Attribute Name (Reveal(x) 360) | Identity Provider Attribute Name (Okta) |
|---|---|
| urn:oid:0.9.2342.19200300.100.1.3 | user.email |
| urn:oid:2.5.4.4 | user.lastName |
| urn:oid:2.5.4.42 | user.firstName |
Configure attributes for system access
You must configure attributes on your identity provider to grant users access to the ExtraHop system. You can type any name for these attributes, but they must match what you configure later in Reveal(x) 360.
| Important: | Attribute values must be less than 2,000 characters. |
- In the application attribute mapping section, add three attributes.
- In the first attribute, select custom or similar and type a descriptive name for user privileges, such as writelevel.
- For the Service Provider, type a descriptive term to identify the attribute in Reveal(x) 360, such as write.
- In the second attribute, select custom or similar and type a descriptive name, such as packetslevel.
- For the Service Provider, type a descriptive term to identify the attribute in Reveal(x) 360, such as packets.
- In the third attribute, select custom or similar and type a descriptive name, such as detectionslevel.
- For the Service Provider, type a descriptive term to identify the attribute in Reveal(x) 360, such as detections.
- Save the settings and then export the application metadata XML file.
| Service Provider Attribute Name (Reveal(x) 360) | Identity Provider Attribute Name (IdP) |
|---|---|
| write | writelevel |
| packets | packetslevel |
| detections | detectionslevel |
Configure your identity provider information in Reveal(x) 360
Assign privileges to users in your IdP
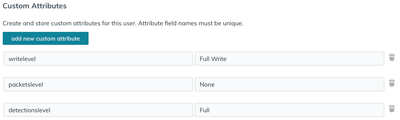
You can now add system access attributes and their associated privilege levels to your existing users. You can assign multiple privileges to a user, but the user is always granted the highest privilege when they log in to the system.
| Tip: | The ExtraHop system supports group attribute statements to easily map user privileges to all members of a specific group. When you configure the ExtraHop application on your identity provider, specify a group attribute name. This name is then entered in the Attribute Name field when you configure the identity provider on the ExtraHop system. |
- In your IdP, select the user you want to grant privileges to.
- Add an attribute for the type of access you previously defined, such as writelevel, packetslevel, or detectionslevel.
- In the same row, add the name you specified for the privilege level, such as Full Write.
Thank you for your feedback. Can we contact you to ask follow up questions?