Tune detections
Detection tuning enables you to reduce noise and surfaces critical detections that require immediate attention.
There are two ways to tune detections: you can add tuning parameters that suppress detections from ever being generated, or you can create tuning rules that hide existing detections based on detection type, participants, or detection properties.
| Video: | See the related training: Configure Tuning Rules |
Tuning Parameters
Tuning parameters enable you to specify known and trusted domains, DNS servers, and HTTP CONNECT targets that should not generate a detection. You can also enable tuning parameters that suppress frequent and redundant detections associated with gateway devices and tor nodes.
Tuning parameters are managed from the Tuning Parameters page and trusted domains are managed from the Network Localities page.
Tuning Rules
Tuning rules enable you to specify criteria that hide detections that have been generated, but are of low-value and do not require attention.
| Note: | Tuning rules might not hide certain detections if your packet sensors are not running the same firmware version as your console. |
- Hidden detections do not cause related triggers and alerts to run while the rule is enabled.
- Hidden detections do not appear as detection markers in charts.
- Hidden detections do not appear on activity maps, but hidden participants will appear in investigation maps.
- Hidden detections do not appear in detection counts on related pages, such as the Device Overview page or the Activity page.
- Hidden detections and participants do not appear in the Executive Report.
- Hidden detections are not included in email and webhook notifications.
| Note: | If you do not see detection markers for any detections, confirm that detection markers have not been disabled. |
Tuning best practices
It is better to create a single parameter or rule that is more broad instead of creating multiple overlapping parameters and rules.
- Start by adding tuning parameters to avoid detections that involve known or trusted agents. Be sure to review the Tuning Parameters and Network Localities pages for existing parameters to avoid redundancy.
- Determine if you want to hide all detections for a specific participant, such as a vulnerability scanner, and select All detection types. If you want to hide by device role, increase the scope to device group.
-
When an IP Address or CIDR Block is selected in the Offender or Victim dropdown, add or remove entries from the list in the IP Addresses field to increase or reduce the scope of the tuning rule.
-
By default, tuning rules expire after 8 hours. You can select a different expiration time from the dropdown or select a new expiration time after you re-enable an expired rule from the Tuning Rules page.
- The ExtraHop system automatically deletes detections that have been on the system for 21 days since the start time of the detection, that are not ongoing, and that are hidden. If a newly created or edited tuning rule hides a detection that matches this criteria, the affected detection will not be deleted for 48 hours.
-
When adding a tuning rule, if you identify a device that is not classified correctly, you can change the device role.
-
Certain detections might require a precise tuning rule based on a specific property of the detection. Under the Property heading, click the checkbox next to a property to specify a value or regular expression and add criteria for a focused tuning rule.
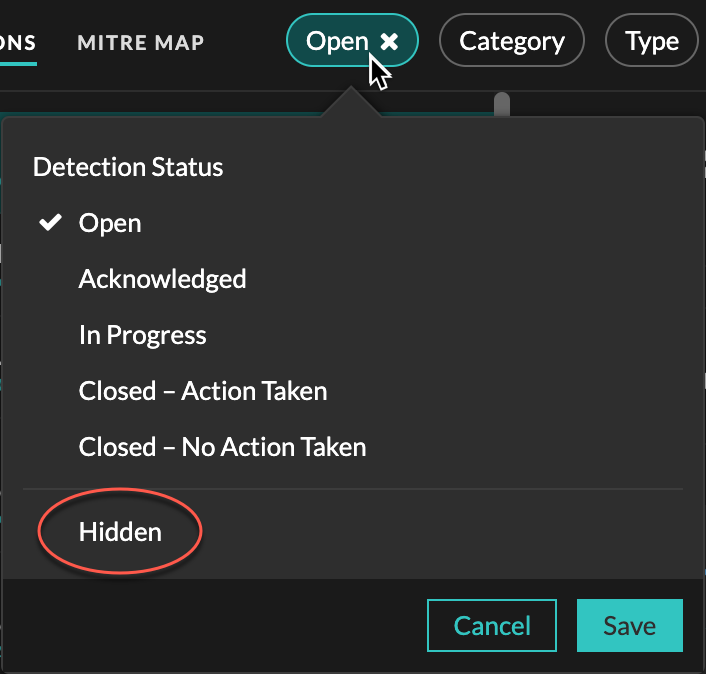
- Apply the Hidden status filter to the Detections page to view detections that are currently hidden by tuning rules.
Learn how to suppress detections with tuning parameters and hide detections with tuning rules.
Thank you for your feedback. Can we contact you to ask follow up questions?