Configure remote authentication through SAML
You can configure secure, single sign-on (SSO) authentication to the ExtraHop system through one or more security assertion markup language (SAML) identity providers.
| Video: | See the related training: SSO Authentication |
| Important: | This guide is only for RevealX Enterprise. For RevealX 360, see Enable sensor access control through your own identity provider. |
When a user logs in to an ExtraHop system that is configured as a service provider (SP) for SAML SSO authentication, the ExtraHop system requests authorization from the appropriate identity provider (IdP). The identity provider authenticates the user's credentials and then returns the authorization for the user to the ExtraHop system. The user is then able to access the ExtraHop system.
Configuration guides for specific identity providers are linked below. If your provider is not listed, apply the settings required by the ExtraHop system to your identity provider.
Identity providers must meet the following criteria:
- SAML 2.0
- Support SP-initiated login flows. IdP-initiated login flows are not supported.
- Support signed SAML Responses
- Support HTTP-Redirect binding
The example configuration in this procedure enables access to the ExtraHop system through group attributes.
If your identity provider does not support group attribute statements, configure user attributes with the appropriate privileges for module access, system access, and packet forensics.
Enable SAML remote authentication
Before you begin
| Warning: | If your system is already configured with a remote authentication method, changing these settings will remove any users and associated customizations created through that method, and remote users will be unable to access the system. Local users are unaffected. |
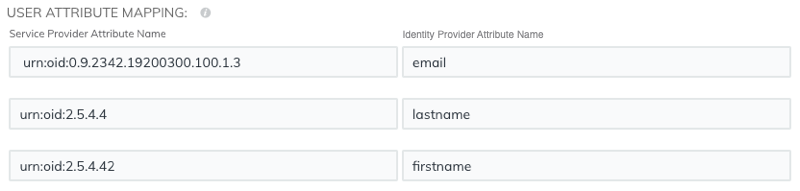
User attribute mapping
You must configure the following set of user attributes in the application attribute mapping section on your identity provider. These attributes identify the user throughout the ExtraHop system. Refer to your identity provider documentation for the correct property names when mapping attributes.
| ExtraHop Attribute Name | Friendly Name | Category | Identity Provider Attribute Name |
|---|---|---|---|
| urn:oid:0.9.2342.19200300.100.1.3 | Standard Attribute | Primary email address | |
| urn:oid:2.5.4.4 | sn | Standard Attribute | Last name |
| urn:oid:2.5.4.42 | givenName | Standard Attribute | First name |
Group attribute statements
The ExtraHop system supports group attribute statements to easily map user privileges to all members of a specific group. When you configure the ExtraHop application on your identity provider, specify a group attribute name. This name is then entered in the Attribute Name field when you configure the identity provider on the ExtraHop system.

If your identity provider does not support group attribute statements, configure user attributes with the appropriate privileges for module access, system access, and packet forensics.
Thank you for your feedback. Can we contact you to ask follow up questions?