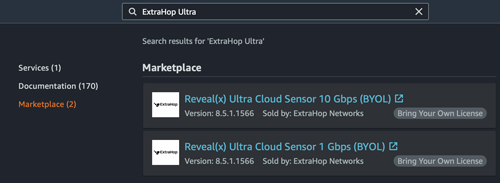
Deploy Reveal(x) Ultra in AWS
In this guide, you will learn how to deploy the ExtraHop Reveal(x) Ultra sensor through AWS Marketplace.
After you deploy the sensor, configure AWS traffic mirroring or remote packet capture (RPCAP) to forward traffic from remote devices to the sensor.
System requirements
Make sure you have everything you need to successfully deploy the sensor:
- An AWS account
- An ExtraHop Reveal(x) Ultra license or product key
- A VPC where the sensor will be deployed
- Two ENI subnets. One subnet to access the management interface of the sensor and one subnet that will forward traffic to the sensor. Both subnets must be in the same Availability Zone.
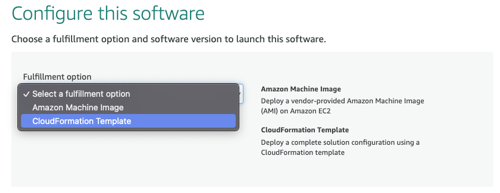
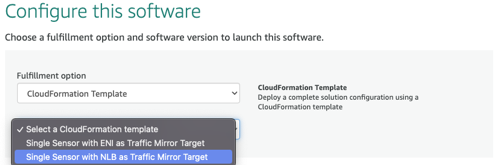
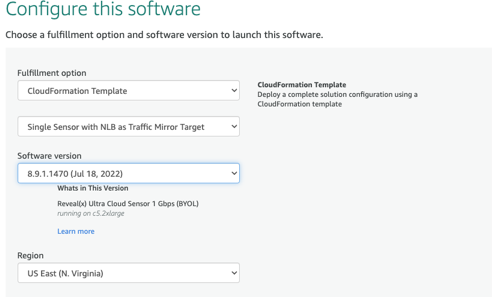
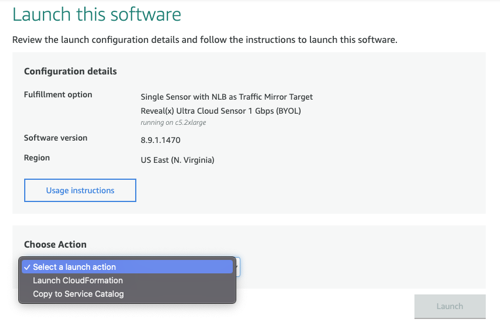
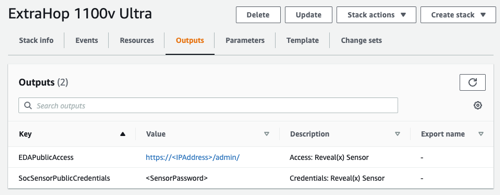
Deploy the sensor
Next steps
- Register your ExtraHop system
- Configure the sensor network interfaces by clicking
Connectivity in the Administration settings. Ensure that
Management is selected on Interface 1. For Interface 2, choose
one of the following options:
- For the 1 Gbps sensor, select Management + RPCAP/ERSPAN/VXLAN/GENEVE Target.
- For the 10 Gbps sensor, select High-Performance ERSPAN/VXLAN/GENEVE Target.
Important: To ensure the best performance for initial device synchronization, connect all sensors to the console and then configure network traffic forwarding to the sensors. - (Recommended) configure AWS traffic mirroring or remote packet capture (RPCAP) to forward traffic from remote devices to the sensor.
- (Optional) Forward GENEVE-encapsulated traffic from an AWS Gateway Load Balancer.
- Complete the recommended procedures in the post-deployment checklist.
Create a traffic mirror target
Complete these steps for each Elastic network interface (ENI) you created.
- In the AWS Management Console, in the top menu, click Services.
- Click .
- In the left pane, under Traffic Mirroring, click Mirror Targets.
- Click Create traffic mirror target.
- (Optional): In the Name tag field, type a descriptive name for the target.
- (Optional): In the Description field, type a description for the target.
- From the Target type drop-down list, select Network Interface.
- From the Target drop-down list, select the ENI you previously created.
- Click Create.
Note the Target ID for each ENI. You will need the ID when
you create a traffic mirror session.
Create a traffic mirror filter
You must create a filter to allow or restrict traffic from your ENI traffic mirror sources to your ExtraHop system.
We recommend the following filtering rules to help avoid mirroring duplicate frames
from peer EC2 instances that are in a single VPC to the sensor.
- All outbound traffic is mirrored to the sensor, whether the traffic is sent from one peer device to another on the subnet or if the traffic is sent to a device outside of the subnet.
- Inbound traffic is only mirrored to the sensor when the traffic is from an external device. For example, this rule ensures that an app server request is not mirrored twice: once from the sending app server and once from the database that received the request.
- Rule numbers determine the order in which the filters are applied. Rules with lower numbers, such as 100, are applied first.
| Important: | These filters should only be applied when mirroring all of the instances in a CIDR block. |
- In the AWS Management Console, in the left pane under Traffic Mirroring, click Mirror Filters.
- Click Create traffic mirror filter.
- In the Name tag field, type a name for the filter.
- In the Description field, type a description for the filter.
- Under Network services, select the amazon-dns checkbox.
- In the Inbound rules section, click Add rule.
-
Configure an inbound rule:
- In the Number field, type a number for the rule, such as 100.
- From the Rule action drop-down list, select reject.
- From the Protocol drop-down list, select All protocols.
- In the Source CIDR block field, type the CIDR block for the subnet.
- In the Destination CIDR block field, type the CIDR block for the subnet.
- In the Description field, type a description for the rule.
- In the Inbound rules sections, click Add rule.
-
Configure an additional inbound rule:
- In the Number field, type a number for the rule, such as 200.
- From the Rule action drop-down list, select accept.
- From the Protocol drop-down list, select All protocols.
- In the Source CIDR block field, type 0.0.0.0/0.
- In the Destination CIDR block field, type 0.0.0.0/0.
- In the Description field, type a description for the rule.
- In the Outbound rules section, click Add rule.
-
Configure an outbound rule:
- In the Number field, type a number for the rule, such as 100.
- From the Rule action drop-down list, select accept.
- From the Protocol drop-down list, select All protocols.
- In the Source CIDR block field, type 0.0.0.0/0.
- In the Destination CIDR block field, type 0.0.0.0/0.
- In the Description field, type a description for the rule.
- Click Create.
Create a traffic mirror session
You must create a session for each AWS resource that you want to monitor. You can create a maximum of 500 traffic mirror sessions per sensor.
| Important: | To prevent mirror packets from being truncated, set the traffic mirror source interface MTU value to 54 bytes less than the traffic mirror target MTU value for IPv4 and 74 bytes less than the traffic mirror target MTU value for IPv6. For more information about configuring the network MTU value, see the following AWS documentation: Network Maximum Transmission Unit (MTU) for Your EC2 Instance. |
Thank you for your feedback. Can we contact you to ask follow up questions?