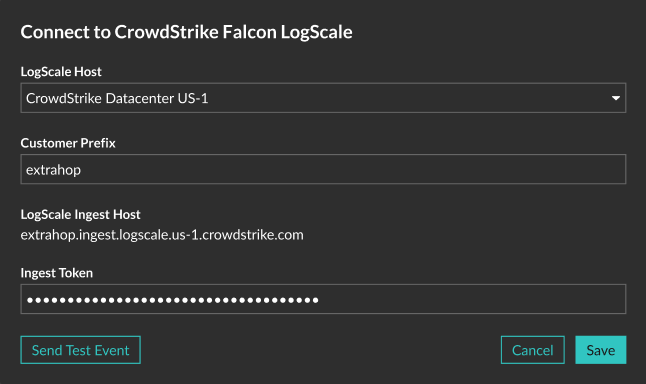
Integrate Reveal(x) 360 with CrowdStrike Falcon LogScale
This integration enables you to export security detections from Reveal(x) 360 to LogScale to view detection data in a centralized system, enhancing context around detections and decreasing the time to confirm threats.
System Requirements
ExtraHop Reveal(x) 360
- Your user account must have privileges on Reveal(x) 360 for System and Access Administration or Cloud Setup.
- Your Reveal(x) 360 system must be connected to an ExtraHop sensor with firmware version 9.3 or later.
- Your Reveal(x) 360 system must be connected to ExtraHop Cloud Services.
CrowdStrike Falcon LogScale
- You must have CrowdStrike Falcon LogScale version 1.92.0 or later.
- You must configure the LogScale HTTP Event Collector API for data ingest.
Thank you for your feedback. Can we contact you to ask follow up questions?