Deploy an ExtraHop Flow Sensor with AWS
This guide explains how to deploy the ExtraHop flow sensor virtual appliance (EFC 1291v) on the Amazon Web Services (AWS) platform.
The EFC 1291v is designed to connect to Reveal(x) 360 and collect flow-based traffic from your network. Packet analysis is not available.
Your environment must meet the following requirements to deploy an EFC 1291v appliance in AWS:
- An AWS account
- Access to the Amazon Machine Image (AMI) of the ExtraHop 1100v appliance
- An EFC 1291v appliance product key
- An AWS instance type that most closely matches the EFC appliance VM size, as
follows:
Appliance Supported Instance Type Reveal(x) EFC 1291v c5.xlarge (4 vCPU and 8 GB RAM)
Deployment overview
Collecting flow logs requires the following configuration setup.
- Configure an IAM policy and IAM role.
- Deploy the ExtraHop flow sensor instance in AWS.
- Download and configure an ExtraHop-supplied Lambda function. The Lambda function runs whenever new flow logs become available and then relays any new events to your sensor. See the following AWS documentation for more information: Using AWS Lambda with Amazon Kinesis Firehose.
- Enable VPC Flow Logs publishing for a set of VPCs in your environment.
- Add a Lambda trigger.
- (Optional): Configure Route 53.
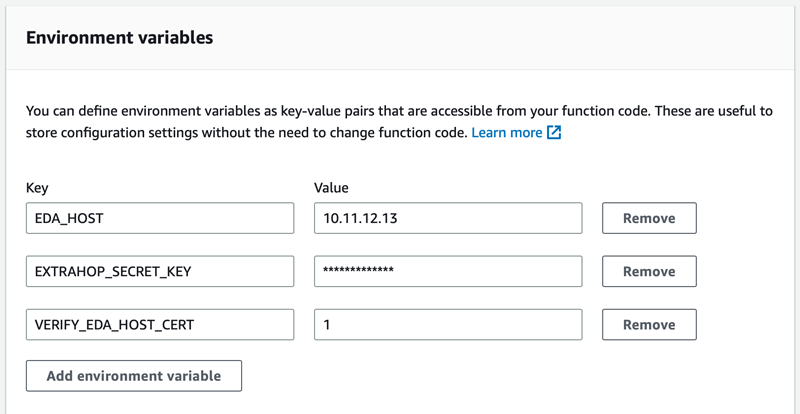
Configure the Lambda function
An ExtraHop-supplied lambda function routes new flow log events to the ExtraHop flow sensor whenever called by a lambda trigger.
For more information about creating Lambda functions, see the AWS documentation.
| Important: | The Lambda function must be on the same VPC and subnet as the flow log sensor. The function must also be part of a security group that allows outbound TCP 443 traffic to the management interface of the collector. |
Create the VPC flow log
Identify the VPCs that you want to monitor with the flow sensor.
- If your ExtraHop AWS deployment includes packet sensors, you should avoid monitoring a particular VPC with both a packet sensor and a flow logs sensor.
- While it is possible to send logs for smaller units like individual subnets or interfaces, sending the entire VPC yields the best discovery of devices.
- Select your VPC.
- Click the Flow logs tab and then click Create flow log
-
Configure the following settings:
Filter: Accept
Maximum aggregation interval: 1 Minute
Destination: Send to Kinesis Firehose in the same account or in a different account
Kinesis Firehose delivery stream name: Select the stream name you created previously
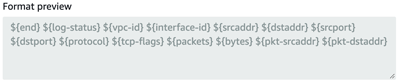
Log record format: Select Custom format and then select the log format attributes in the following order:
- end
- log-status
- vpc-id
- interface-id
- srcaddr
- dstaddr
- srcport
- dstport
- protocol
- tcp-flags
- packets
- bytes
- pkt-srcaddr
- pkt-dstaddr
The format preview should appear similar to the following figure.
Configure Route 53 logs (optional)
Amazon Route 53 provides DNS query logging, which is not required for the flow log configuration but is strongly recommended when the Amazon DNS server is configured.
To configure Route 53 to log DNS queries that originate in your VPCs, see the following AWS documentation: Managing Resolver query logging configurations.
- Go to the Route 53 service.
- In the Resolver section, click Query logging.
- Click Configure query logging.
- Type a query logging configuration name.
- Select Kinesis Data Firehose delivery stream as the query logs destination.
- Select the Kinesis Data Firehose delivery stream that you created previously.
- In the VPCs to log queries for section, click Add VPC.
- Select the VPCs that you want to log queries for and then click Add.
- Click Configure query logging.
Thank you for your feedback. Can we contact you to ask follow up questions?