Configure SAML single sign-on with JumpCloud
You can configure your ExtraHop system to enable users to log in to the system through the JumpCloud identity management service.
Before you begin
- You should be familiar with administering JumpCloud.
- You should be familiar with administering ExtraHop systems.
These procedures require you to copy and paste information between the ExtraHop system and JumpCloud, so it is helpful to have each system open side-by-side.
Enable SAML on the ExtraHop system
- Log in to the Administration settings on the ExtraHop system through https://<extrahop-hostname-or-IP-address>/admin.
- In the Access Settings section, click Remote Authentication.
- From the Remote authentication method drop-down list, select SAML.
- Click Continue.
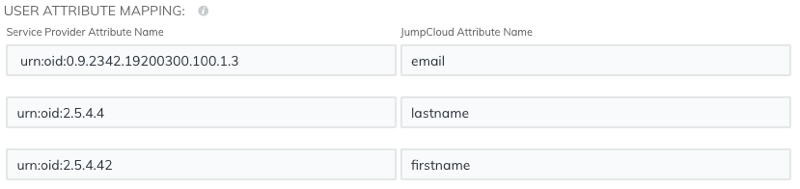
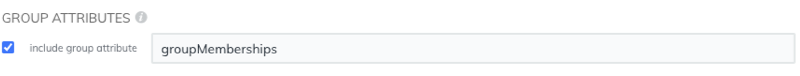
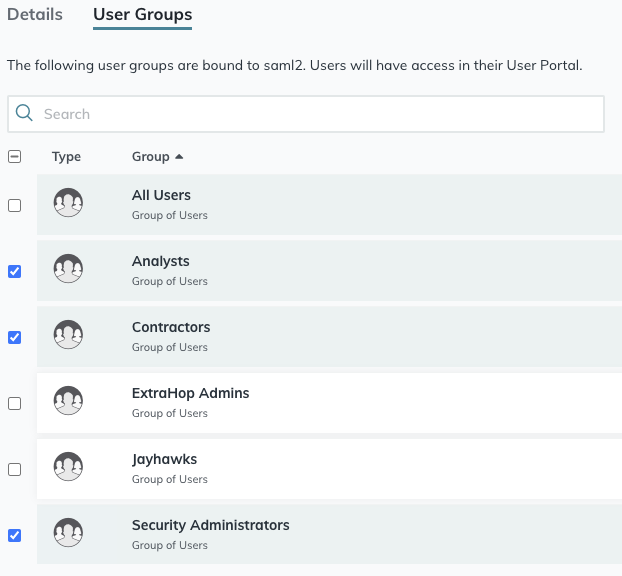
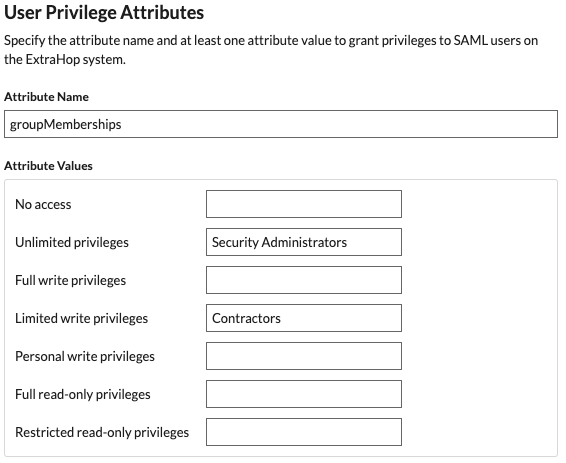
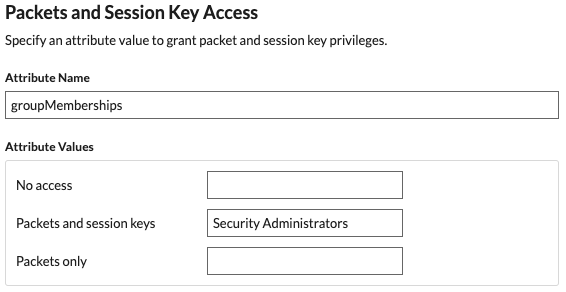
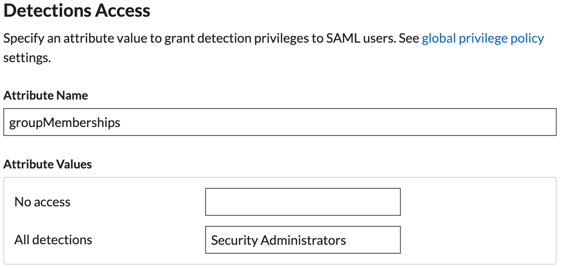
- Click View SP Metadata. You will need to copy the ACS URL and Entity ID to paste into the JumpCloud configuration in the next procedure.
 .
.
Thank you for your feedback. Can we contact you to ask follow up questions?