Deploy Reveal(x) 360 sensors for AWS in advanced environments
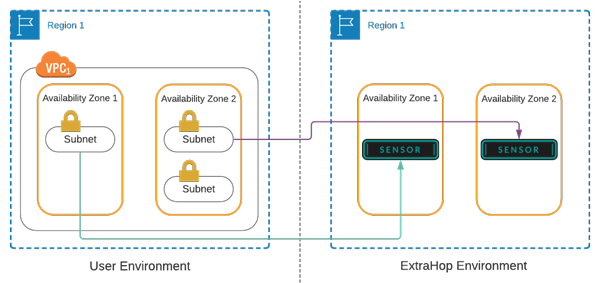
Reveal(x) 360 offers a flexible and highly-customizable environment that enables you to monitor traffic from ENIs in multiple Availability Zones (AZ). In general, you should deploy only the number of sensors necessary for the amount of traffic you want to monitor, however each sensor must be configured for a single AZ. Therefore if you have ENIs in multiple AZs, we recommend that you deploy a sensor for each AZ.
| Note: |
|
The number of mirror target interfaces in a single sensor depends on the sensor size.
| Sensor Size | Number of Mirror Target Interfaces |
|---|---|
| Extra Small Premium or Ultra | 3 |
| Small Premium or Ultra | 3 |
| Medium Premium | 7 |
For simple deployments where you only need to mirror traffic from ENIs in a single Availability Zone (AZ), follow the instructions in the Deploy Reveal(x) 360 sensors for AWS guide.
For more complex environments where you need to mirror traffic from ENIs in multiple AZs to multiple sensors, you must repeat some procedures for the ENIs in each AZ.
The following flow chart shows the recommended order of each procedure.
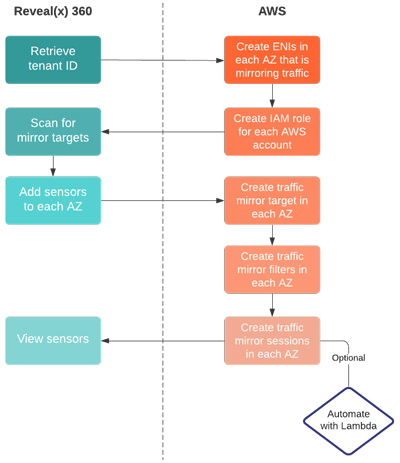
The following steps provide links and guidance for each procedure.
- Retrieve your tenant ID from Reveal(x) 360.
- Create ENIs in each AZ that have the traffic you want to monitor. These ENIs are your mirror target interfaces.
- If you have a single AWS account, create one IAM role. If your AZs span multiple accounts, you must create an IAM role for each account.
- Scan for mirror targets in Reveal(x) 360. Every ENI that you created in an AZ should appear in the list of available mirror targets interfaces.
- Deploy the first sensor for the ENIs in the first AZ, and then repeat this procedure until you have provisioned a sensor for the ENIs in each additional AZ.
- Return to AWS and create a traffic mirror target for the source ENIs in each AZ.
- Create traffic mirror filters to avoid duplicating traffic from the ENIs in each AZ.
-
Create the
traffic mirror sessions for the traffic mirror targets you created in
each AZ.
We recommend that you configure a Lambda function to automatically mirror traffic from your EC2 instances to your sensors.
- Finally, return to the Reveal(x) 360 Console to view your sensor traffic.
Thank you for your feedback. Can we contact you to ask follow up questions?